Intro
I participated in the NahamCon CTF 2024 with the Hack Smarter team and we came in 196th position among almost 4000 teams.
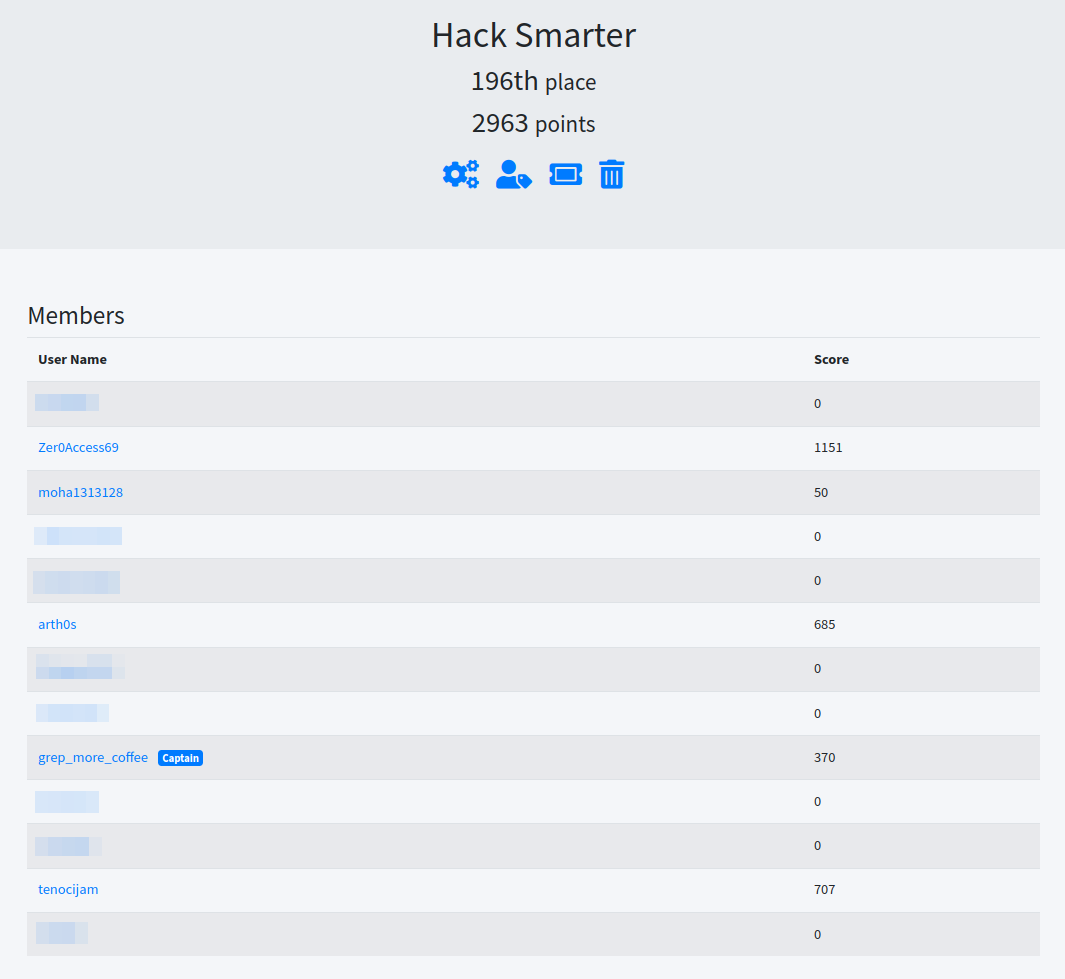
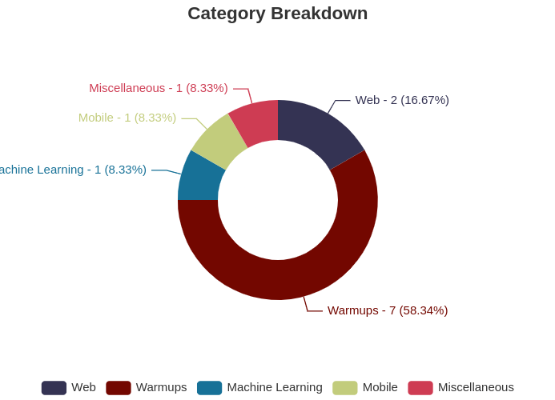
My solves based on categories:
Below is my writeup for some of the challenges in the NahamCon CTF 2024:
All About Robots🤖
Author: @JohnHammond
Category: Web
Difficulty: Easy
Description:
Oh wow! Now you can learn all about robots, with our latest web service, All About Robots!!
Connect with: http://challenge.nahamcon.com:32155
The website looks like this:
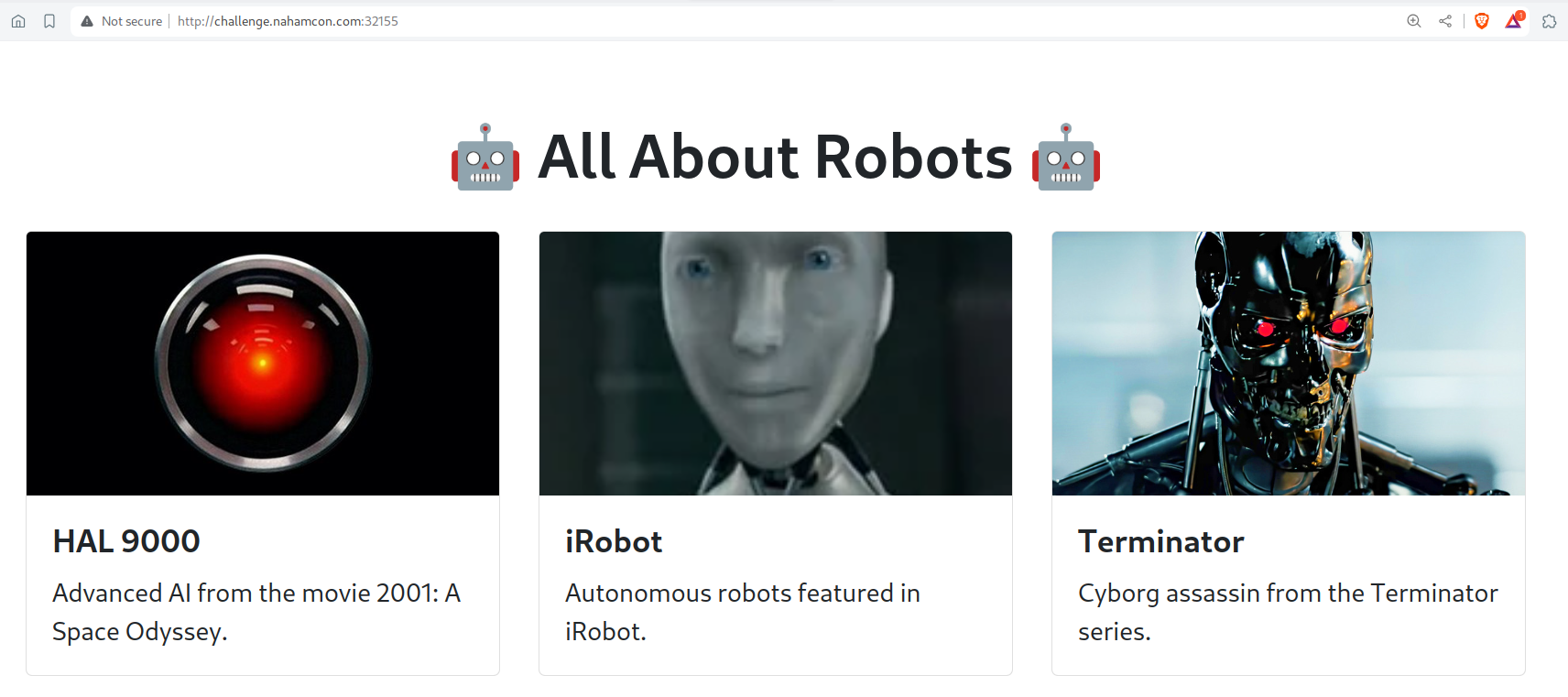
The title and the description of this challenge highlights the word robots.
By doing a Google search on “robots in websites”, we see about the robots.txt file.
This is a text file used by websites to communicate with web crawlers and other web robots. This file tells the crawlers which parts of the website they are allowed or disallowed to access and crawl.
We can check the robots.txt by visiting http://challenge.nahamcon.com:32155/robots.txt. We can see that there is one path (/open_the_pod_bay_doors_hal_and_give_me_the_flag.html) which is disallowed and by navigating to that path we will get our flag for the challenge.
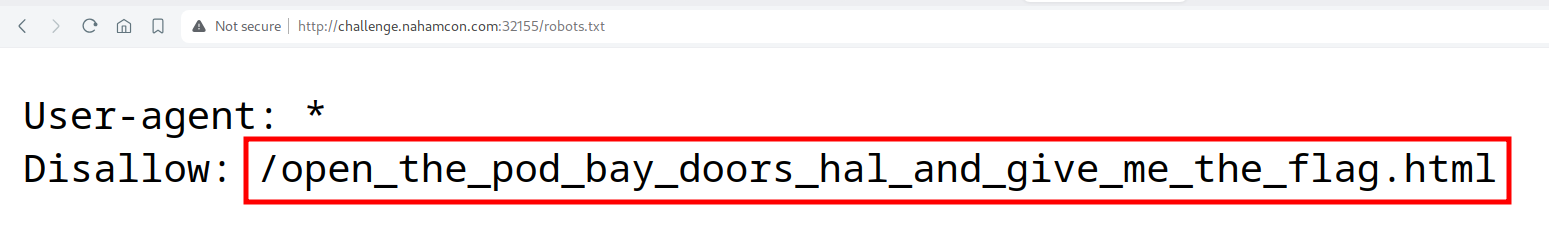
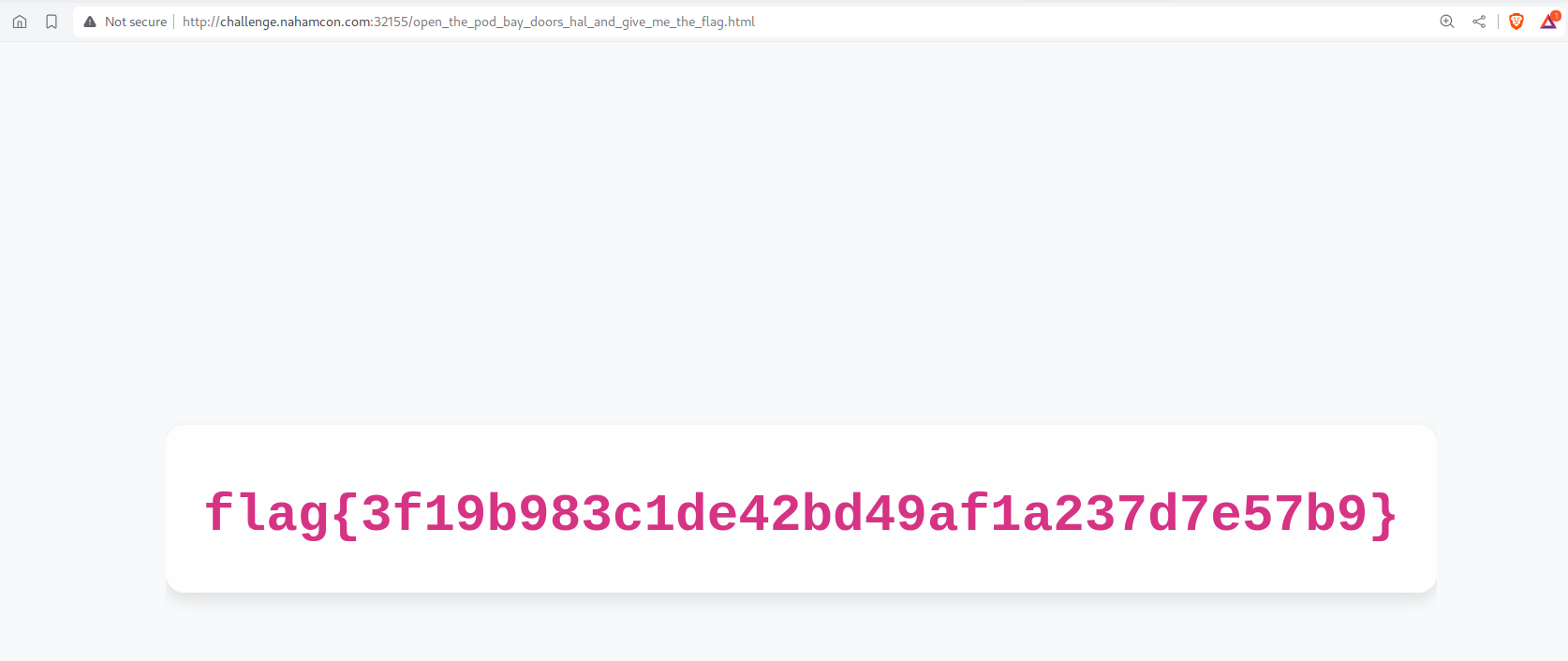
Flag:
flag{3f19b983c1de42bd49af1a237d7e57b9}
Read The Rules📜
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
Please follow the rules for this CTF!
We can visit the rules page of this CTF and check the page source to get the flag
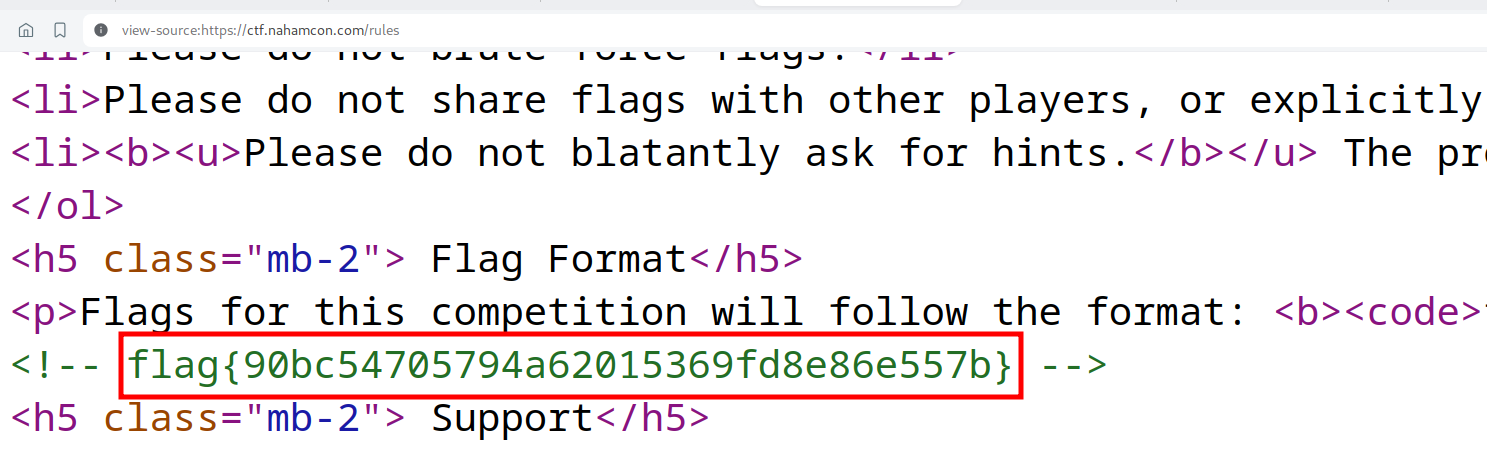
Flag:
flag{90bc54705794a62015369fd8e86e557b}
Technical Support🤝
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
Want to join the party of GIFs, memes and emoji shenanigans? Or just want to ask a question for technical support regarding any challenges in the CTF?
This CTF uses support tickets to help handle requests. If you need assistance, please create a ticket with the
#ctf-open-ticketchannel. You do not need to direct message any CTF organizers or facilitators, they will just tell you to open a ticket. You might find a flag in the ticket channel, though!Connect here: Join the Discord!
The flag is available in the #ctf-open-ticket channel of nahamsec Discord
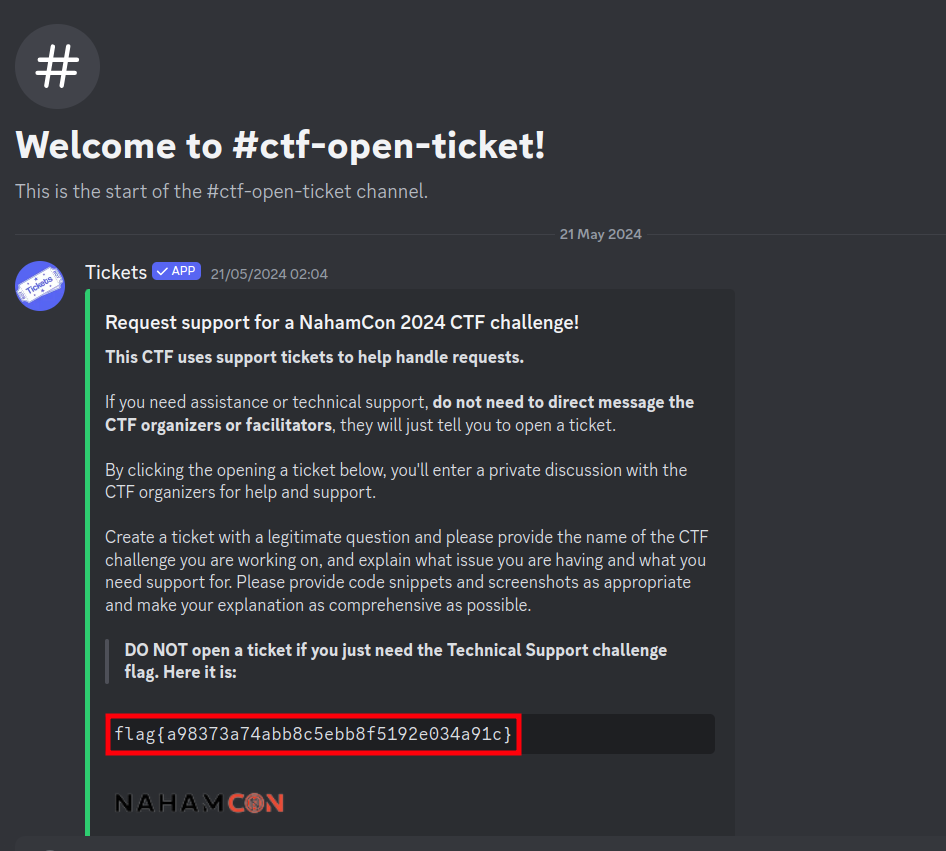
Flag:
flag{a98373a74abb8c5ebb8f5192e034a91c}
QRRRRRRRR𝄃𝄃𝄂𝄂𝄀𝄁𝄃𝄂𝄂𝄃
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
Wait a second, they made QR codes longer!?!
Below is the provided QR Code:

This type of QR code is called rMQR (Rectangular Micro QR Code). We can scan this QR code using QRQR - QR Code® Reader app for both Android and iOS.
Flag:
flag{a44557e380e3baae9c21c738664c6142}
Copypasta📄
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
You know those funny Internet messages that everybody likes to copy and paste? Yeah….
Turns out they make a good Warmups CTF challenge, too!
Connect with:
nc challenge.nahamcon.com 31476
After connecting to the server, we get back a bunch of text with the flag hidden within it. The flag is made hidden by making the color of the text same as the background color. We can see the flag after copy pasting the text into any text editor.
Flag:
flag{1f68e019b29650f6e8ea15a7808f76fd}
*I was not able to connect to the service during the time of writing this writeup, that is the reason no screenshots are provided
EICAR🔢
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
What is the MD5 hash of this file?
Wrap the hexadecimal value in the flag{ prefix and { suffix to match the standard flag format.
Note, your antivirus engine might flag this file – don’t worry, I promise it’s not malware :)
After downloading the given attachment, we can find out its MD5 hash using below command in linux:
md5sum eicar
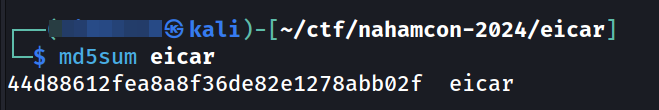
We can put this in the flag format and submit the flag.
Flag:
flag{44d88612fea8a8f36de82e1278abb02f}
iDoor🪪
Author: @JohnHammond
Category: Web
Difficulty: Easy
Description:
It’s Apple’s latest innovation, the “iDoor!” … well, it is basically the Ring Doorbell camera, but the iDoor offers a web-based browser to monitor your camera, and super secure using ultimate cryptography with even SHA256 hashing algorithms to protect customers! Don’t even think about snooping on other people’s cameras!!
Connect with: http://challenge.nahamcon.com:31646
On visiting the website we can see that our Customer ID is 11 and if we closely look at the URL, it looks like there is a SHA256 hash value (hint from challenge description). The SHA256 value decodes to the number 11.
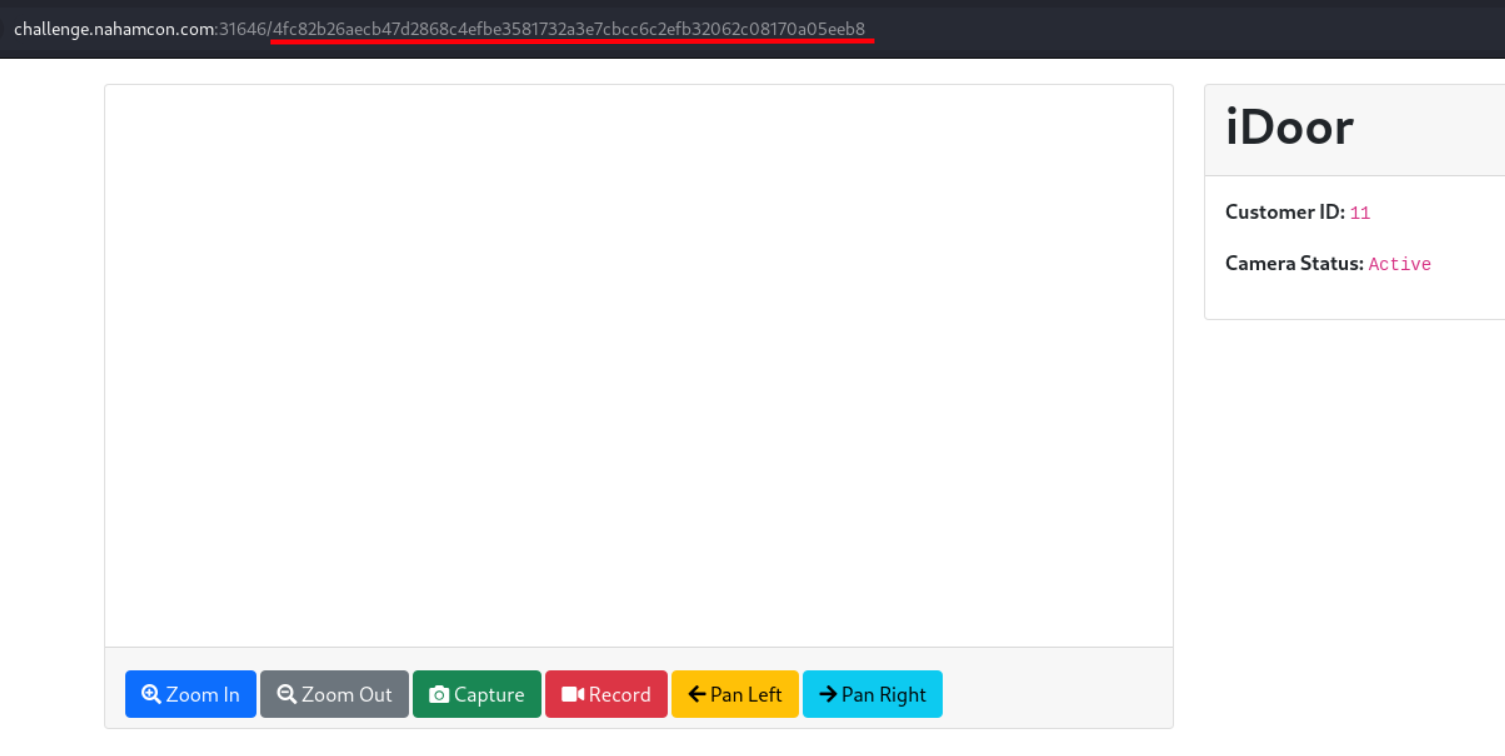
IDOR (Insecure Direct Object Reference) is a security vulnerability which allows users to access data or functions directly through a reference like a URL or a parameter, without proper authorization checks.
With that in mind we can try to access other customer page by changing the hash value in the URL to the SHA256 hash of any number.
We will get the flag if we use the SHA256 hash value of 0.
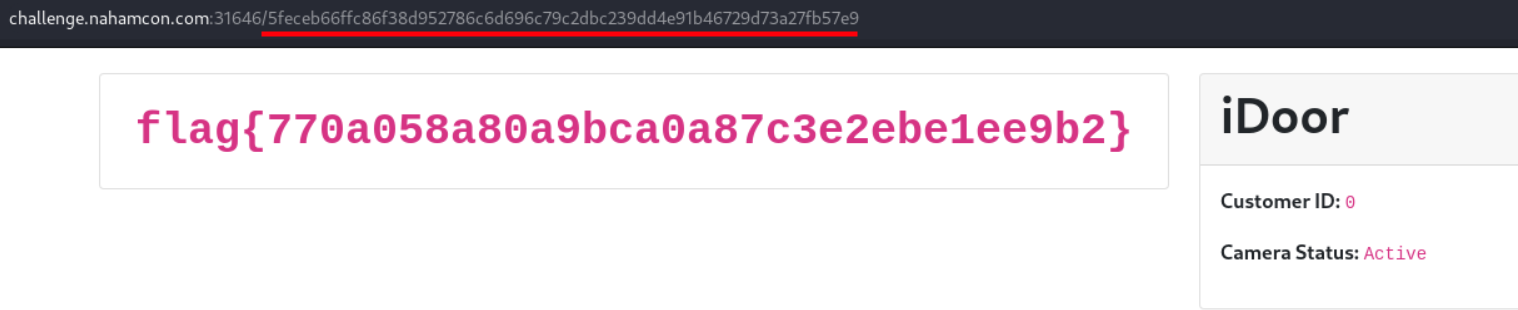
Flag:
flag{770a058a80a9bca0a87c3e2ebe1ee9b2}
That’s Not My Base🔢
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
Everyone knows about Base64, but do you know about this one?
(Remember, the flag format starts with flag{!)
F#S<YRXdP0Fd=,%J4c$Ph7XV(gF/*]%C4B<qlH+%3xGHo)\
I put this string of text in CyberChef and tried decoding from all available base types, base92 worked!
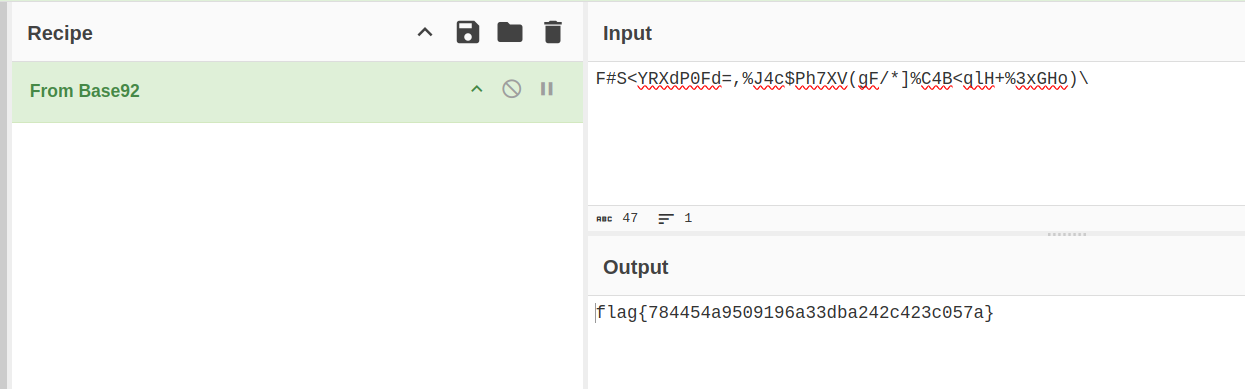
Flag:
flag{784454a9509196a33dba242c423c057a}
Twine🧵
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
Google tells me that twine means: “strong thread or string consisting of two or more strands of hemp, cotton, or nylon twisted together.”
One attachment called “twine.jpg” is provided

I noticed the word string in the description and used strings command on the file.
strings is used to display printable character sequences from files.
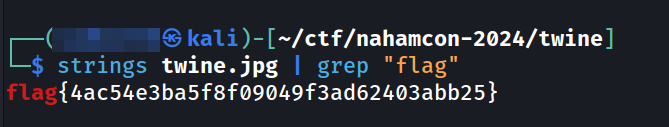
Just using strings will output a lot of text, so we can use grep to filter and output only the text containing the word “flag”
Command:
strings twine.jpg | grep "flag"
Flag:
flag{4ac54e3ba5f8f09049f3ad62403abb25}
Uriel🔗
Author: @JohnHammond
Category: Warmups
Difficulty: Easy
Description:
Uriel was browsing the web and he saw this big long blob of text in his address bar! He was telling me about it but I don’t remember everything he said… I think he mentioned something like “it happened twice?”
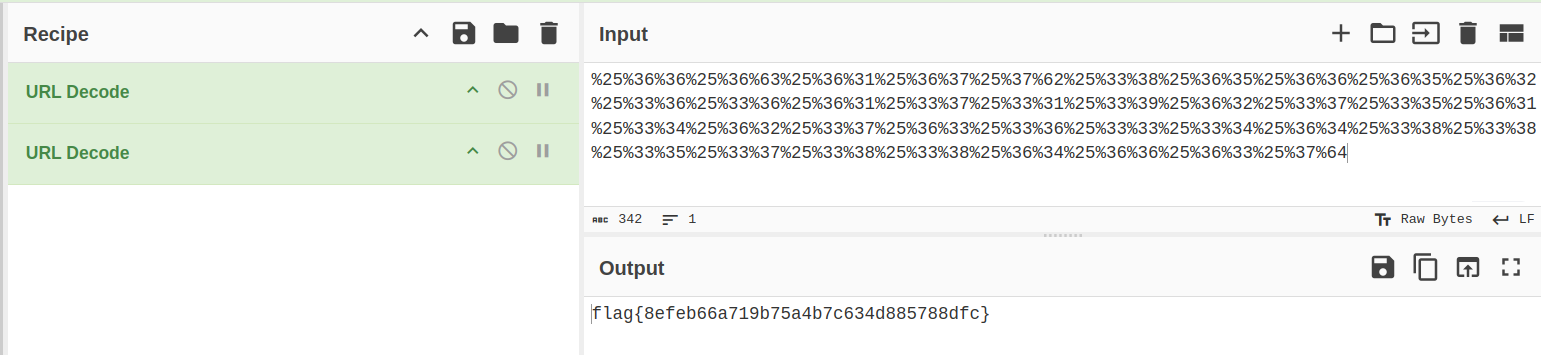
%25%36%36%25%36%63%25%36%31%25%36%37%25%37%62%25%33%38%25%36%35%25%36%36%25%36%35%25%36%32%25%33%36%25%33%36%25%36%31%25%33%37%25%33%31%25%33%39%25%36%32%25%33%37%25%33%35%25%36%31%25%33%34%25%36%32%25%33%37%25%36%33%25%33%36%25%33%33%25%33%34%25%36%34%25%33%38%25%33%38%25%33%35%25%33%37%25%33%38%25%33%38%25%36%34%25%36%36%25%36%33%25%37%64
The given text looks like it is URL encoded because of the use of percentage signs. So I decoded it using CyberChef twice (hint from description) and got the flag
Flag:
flag{8efeb66a719b75a4b7c634d885788dfc}
Kitty Kitty Bang Bang🐱
Author: @matlac
Category: Mobile
Difficulty: Easy
Description:
I found a cool android app to play with a cowboy cat! There’s has to be more going on with the app I can’t see on my screen…
The apk file named com.nahamcon2024.kittykittybangbang.apk was also provided.
I installed this apk on my phone and ran it. It is a simple application that displays a “BANG!” image and plays a sound when we tap on the screen.
I then analyzed the apk using jadx-gui and found that inside a function inside MainActivity, it logs the flag each time we tap the screen.
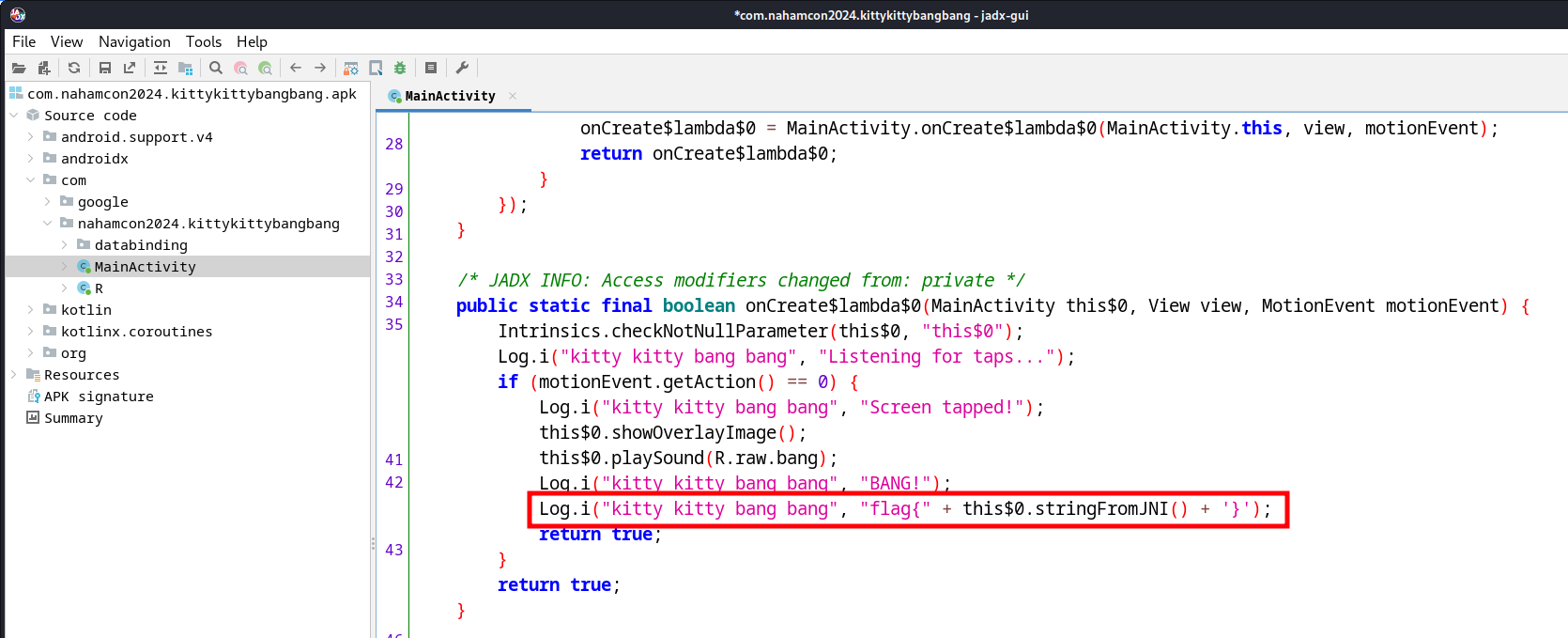
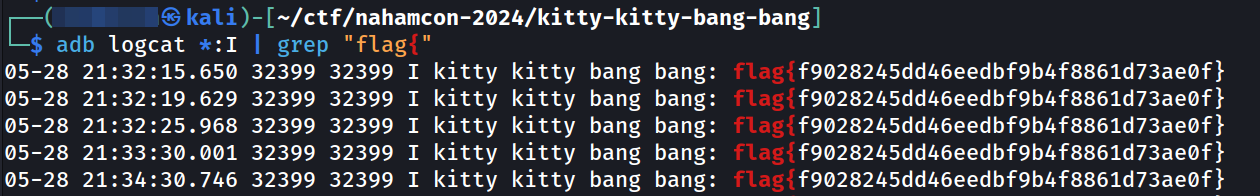
Then I connected my phone to my PC and used below command to display all informational log messages and filter text containing only “flag{”
adb logcat *:I | grep "flag{"
Flag:
flag{f9028245dd46eedbf9b4f8861d73ae0f}
Indicium🔡
Author: @kkevsterrr
Category: Machine Learning
Difficulty: Medium
Description:
Rwa Kuv, if you catch my drift.
103, 109, 98, 104, 124, 99, 99, 50, 54, 53, 99, 101, 103, 49, 49, 51, 98, 55, 51, 49, 101, 99, 55, 54, 56, 99, 57, 101, 103, 57, 53, 98, 57, 56, 49, 55, 53, 126
These looked like ASCII codes to me, so I tried converting these ASCII codes to their respective characters.
Python script to convert ascii value to character:
codes = [103, 109, 98, 104, 124, 99, 99, 50, 54, 53, 99, 101, 103, 49, 49, 51, 98, 55, 51, 49, 101, 99, 55, 54, 56, 99, 57, 101, 103, 57, 53, 98, 57, 56, 49, 55, 53, 126]
for code in codes:
print(chr(code), end="")
Output:
gmbh|cc265ceg113b731ec768c9eg95b98175~
Above text is somewhere similar to our flag format and by bringing down each character by 1 position we will get our correct flag.
Python script to get the final flag:
codes = [103, 109, 98, 104, 124, 99, 99, 50, 54, 53, 99, 101, 103, 49, 49, 51, 98, 55, 51, 49, 101, 99, 55, 54, 56, 99, 57, 101, 103, 57, 53, 98, 57, 56, 49, 55, 53, 126]
for code in codes:
print(chr(code-1), end="")
Flag:
flag{bb154bdf002a620db657b8df84a87064}
Not Quite The Same🖼️
Author: @Kkevsterrr
Category: Miscellaneous
Difficulty: Medium
Description:
Everyone knows MD5 hashes. Everyone knows
.pngfiles! I believe you’ll collide with greatness.Connect with: http://challenge.nahamcon.com:31875
The website allows us to upload 2 .png files.
The challenge description gives us a hint about MD5 collisions. MD5 collision occurs when two different sets of data produce the same MD5 hash value.
So in this case, we will get the flag if we upload 2 .png files with the same MD5 hash.
Two .png files having same MD5 hash value can be obtained from here.
We will get the flag after uploading both the images to the website.
*I was not able to connect to the service during the time of writing this writeup, that is the reason no screenshots are provided
